What is Penetration Testing?
As cyber threats continue to evolve, it is imperative for companies to stay ahead of potential attackers. One of several key tools used by organisations across all sectors today is penetration testing. The aim of this proactive approach to security is to help organizations identify vulnerabilities before malicious actors can exploit them.
Penetration testing evaluates the security of an IT infrastructure by safely attempting to identify exploitable vulnerabilities. These weaknesses can exist in operating systems, services, applications, and configurations. The primary goal of penetration testing is to uncover security gaps and provide actionable insights to improve the overall security posture. By simulating cyberattacks, penetration testing identifies vulnerabilities that malicious actors could exploit, allowing businesses to enhance their security measures proactively over time.
Contact us today
We provide 360° protection of your assets & people against strategic cyber risk.
+41 58 458 7788
E-Mail
Why Penetration Testing is Essential
Penetration testing is not just a technical exercise, it is a crucial component of effective cybersecurity and compliance strategies today. Here are some key reasons why penetration testing is essential:
- Identify Security Gaps: Penetration tests simulate real-world attacks, revealing security gaps that automated tools might miss. This thorough examination helps organizations understand their vulnerabilities and the potential impact of an attack.
- Enhance Risk Management: By identifying and addressing vulnerabilities, organizations can better manage risks. Penetration testing provides a clear picture of the security landscape, allowing for informed decision-making and prioritization of security investments.
- Ensure Compliance: Many industries have regulatory requirements that mandate regular penetration testing. Conducting these tests helps organizations comply with standards and regulations, avoiding potential fines and legal issues.
- Improve Incident Response: Penetration testing helps organizations enhance their incident response capabilities. By understanding how an attack might occur, teams can develop and refine their response strategies to minimize damage and recovery time.
- Protect Reputation: A security breach can significantly damage an organization’s reputation. Penetration testing helps prevent breaches, protecting the organization's reputation and maintaining customer trust.

Penetration Testing for Large Organizations
For larger organizations, penetration testing can also be utilised to evaluate the performance and value of investments in advanced solutions such as Extended Detection and Response (XDR) and Security Operations Center (SOC) teams. By simulating sophisticated attacks, penetration testing can reveal how well these systems detect, respond to, and mitigate threats, ensuring that the implemented cybersecurity measures are aligned to the organisation’s requirements, and are delivering value moreover.
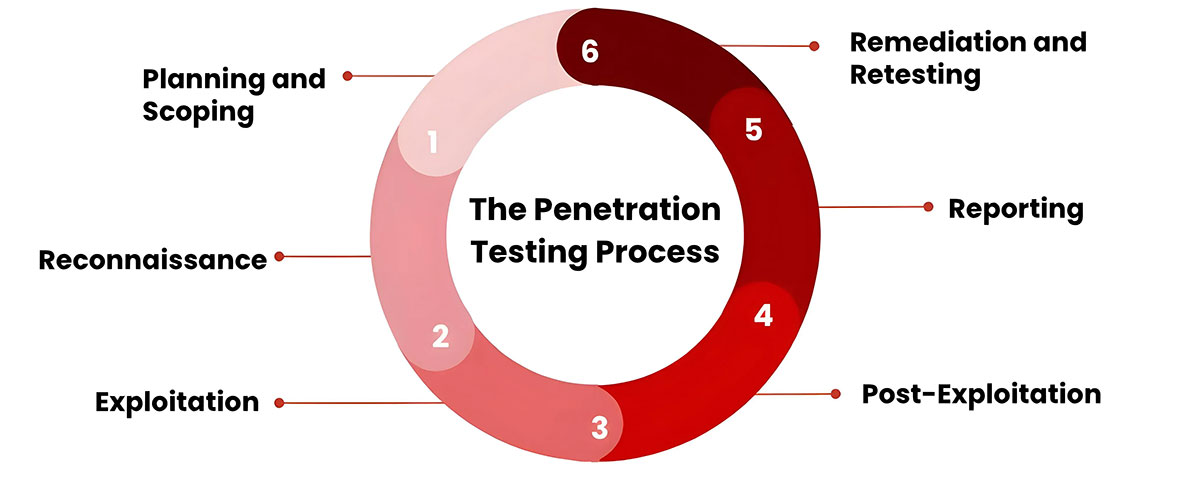
The Penetration Testing Process
Penetration testing involves several steps to ensure a comprehensive evaluation of security defenses:
- Planning and Scoping: Defining the goals and scope of the penetration testing, including determining which systems will be tested and identifying the specific techniques and tools to be used.
- Reconnaissance: Gathering of information about the target systems, including network scanning, social engineering, and public information gathering.
- Exploitation: The execution of techniques to exploit the identified vulnerabilities, simulating an actual attack to understand how far an attacker can penetrate the organisation’s systems and environments.
- Post-Exploitation: Analysis of the extent of the compromise, including determining what data can be accessed and the potential impact on the organization of unauthorised access, theft, denial of access or other disruption.
- Reporting: Documenting findings in a detailed report, including identified vulnerabilities, the methods used, details of exploitation and its implications, and recommendations for remediation.
- Remediation and Retesting: Addressing the identified vulnerabilities and retesting to ensure that the issues have been resolved, strengthening overall resilience against cybersecurity and compliance related security risks.
Best Practices for Effective Penetration Testing
To maximize the benefits of penetration testing, organizations should follow these best practices:
- Regular Testing: Conduct penetration tests regularly, especially after significant changes to the IT environment. Regular testing helps identify new vulnerabilities and ensures continuous improvement.
- Use Skilled Professionals: Engage experienced and certified penetration testers. Skilled professionals can provide deeper insights and more effective testing methodologies.
- Comprehensive Scope: Ensure that the scope of the penetration test covers all critical systems and potential attack vectors. A comprehensive scope helps identify vulnerabilities across the entire IT infrastructure.
- Actionable Reporting: Focus on creating actionable reports that provide clear and prioritized recommendations. This helps organizations effectively address vulnerabilities and improve their security posture.
- Integrate with Overall Risk Management: Align penetration testing with the organization's overall risk management strategy. This integration ensures that security efforts are focused on the most critical risks.
Contact us today for tailored penetration testing services
Teichmann International (IT Solutions) AG offers penetration testing as a standalone service or as part of our Red Teaming and more comprehensive Security Monitoring services. Whether for compliance auditing, cyber risk assessment to enable security transformation, or used as a component of a more comprehensive cyber risk management services and support, we can provide penetration testing to meet your requirements for any scenario.
Contact us today to find out how Teichmann International (IT Solutions) AG can help you meet your compliance and cyber resilience objectives.

