As the potential costs of cyber threats facing organizations today continues to rise, effective IT Vulnerability Management is vital for mitigating risk on an ongoing basis and helping to ensure the security of digital assets. Today IT Vulnerability Management involves a continuous cycle of steps and associated measures as outlined below.
We provide 360° protection of your assets & people against strategic cyber risk.
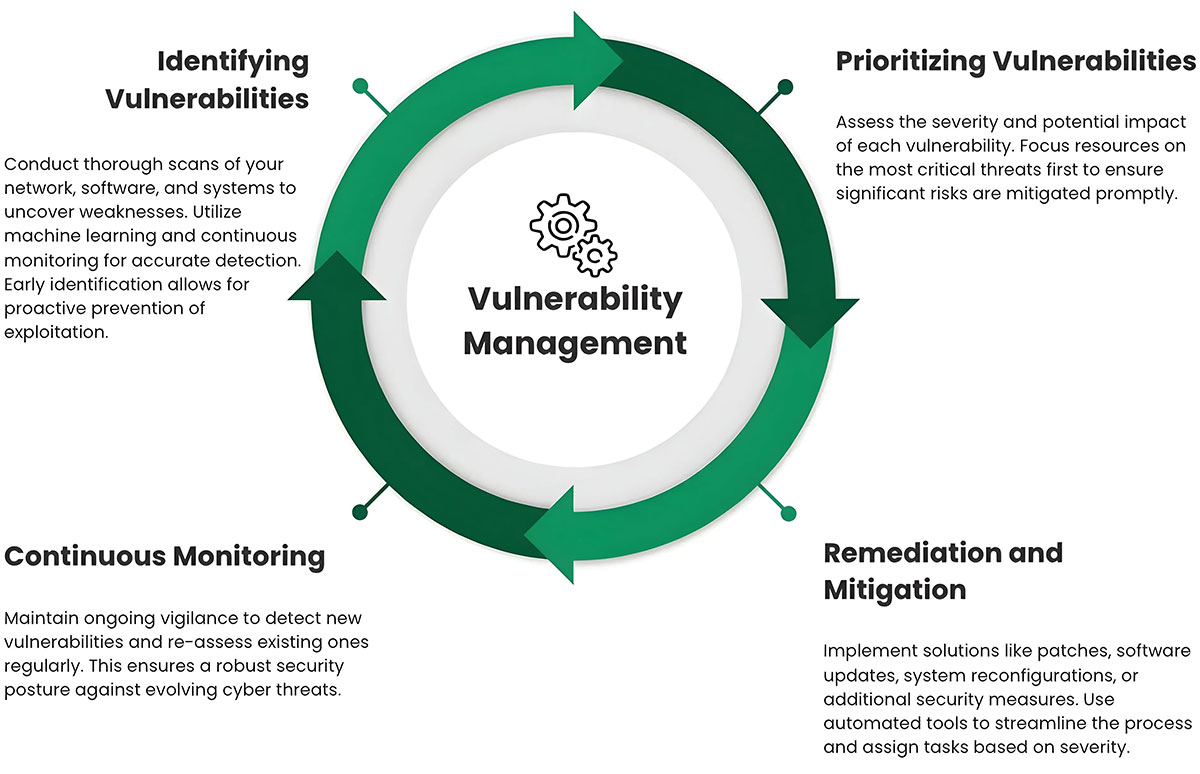
+41 58 458 7788 E-MailThe first step in IT Vulnerability Management is identification. This involves conducting thorough scans of your network, software, and systems to uncover potential weaknesses. Advanced IT Vulnerability Management systems utilize machine learning and continuous monitoring to detect vulnerabilities with high accuracy. By identifying vulnerabilities early, organizations can take proactive measures to prevent exploitation.
Once vulnerabilities are identified, the next step is prioritization. Not all vulnerabilities pose the same level of risk. Effective vulnerability management involves assessing the severity and potential impact of each vulnerability. This prioritization process allows organizations to focus their resources on addressing the most critical threats first, ensuring that the most significant risks are mitigated promptly.
After prioritization, the focus shifts to remediation and mitigation. This step involves implementing solutions to address the identified vulnerabilities. Solutions may include applying patches, updating software, reconfiguring systems, or implementing additional security measures. Automated remediation tools can streamline this process, generating and assigning remediation tasks based on the severity and nature of each vulnerability.
Vulnerability management is not a one-time effort but a continuous process. Continuous monitoring ensures that new vulnerabilities are detected as they emerge and that existing vulnerabilities are re-assessed regularly. This ongoing vigilance is essential for maintaining a robust security posture in the face of evolving cyber threats.

Implementing a robust vulnerability management strategy offers several key benefits:
Since organizations can often struggle to maintain an effective Vulnerability Management program, many increasingly opt for turnkey IT Vulnerability Management as a Service for the assurance of a dedicated, specialised capability, and the added benefit of freeing up more organizational resources to focus on business operations.
Effective IT vulnerability management is a critical component of any comprehensive cybersecurity strategy. By identifying, prioritizing, and addressing vulnerabilities, organizations can significantly reduce their risk of attacks.
Vulnerability Management as a Service: as part of a managed SOC-as-a-Service offering delivered by expert security teams actively monitoring your organisation’s attack surfaces 24/7 for vulnerabilities.
Patch Management: best-of-breed software enabling you to adopt an automated Vulnerability Management solution.
Digital Forensics Service: Our digital forensics service can be utilised as a pre-emptive protective measure to discover vulnerabilities before they can be fully exploited by attackers.
Dark Web Monitoring: Our dark web monitoring service offers early detection of potential threats, allowing you to take proactive measures to protect your organization.